Monday, September 29, 2008
Access two servers using same domain name
Right now when I am on my internal network I can go to http://192.168.1.2 in my web browser and the web based application will open. I know that an address of 192.168.x.x will not work outside of our local network. I want to be able to access the application that is on 192.168.1.2 from the Internet. So, from the outside, I want to be able to go to www.mydomain.com, then have a link on our company website that will point them to the application on the other server. I would like our visitors to stay within our same domain. I can add a virtual directory in IIS on the website server that points to the web folder on the application server. Am I going down the right path with a virtual directory?
Ans -
If you have a separate dns entry for the 2nd application you could use host headers on the main server and have the 2nd domain get redirected to the 2nd server.
Or you could just identify a virtual directory in the main server and put some asp redirect that shuffles everything to the 2nd server.
Or if both computers are on the same lan, you could just let the main server be the only webserver using a virtual directoy mapped to the other server.
__________________
More...
http://forums.devshed.com/iis-97/redirect-to-another-internal-webserver-317863.html
Using the Windows Server 2003 Computer Management Console Event Viewer snap-in
(To access the Computer Management Console in Windows Server 2003, right-click the My Computer Icon on the Start menu and select Manage with the left button.)
Event Viewer displays items logged by the system when actions happen within a Windows Server 2003 system. You can access the tool from the Run dialog by entering eventvwr and clicking OK.
By default, the events logged are captured in one of these log files:
|> System: Shows Windows system events.
|> Application: Shows events recorded by applications that are installed on the system.
|> Security: Contains records of logon/logoff actions and privilege use.
(Other applications -- which include later versions of Microsoft Office and Internet Explorer, Microsoft Active Directory, and File Replication Services -- may create their own logs, which will appear in the event log.)
Each of the logs included in Event Viewer by default allow you to quickly view actions taking place on a system. For example, the starting and stopping of services are recorded as informational entries in the System log.
The System and Application logs also record warning events and critical events. Warning events display events that are not immediate problems but could cause more serious issues if left unchecked. Critical events occur when a component or application fires an error when performing a task. An example of a critical event within the Directory Services log might be an error that occurs when the Domain Controllers in your Active Directory environment cannot replicate directory service information between each other. While this error can be caused by several things, including network outages or problems with DNS, it is classified as critical because it becomes a significant point of possible failure in your environment.
Backing up, clearing, and altering the size of event logs
You can also use Event Viewer to back up and clear the event logs. You may want to do this if a given log has reached its maximum size limit.
To clear a log of all the events it currently holds, follow these steps:
|>In the left pane of the Computer Management Console, right-click the event log you want to clear and select Clear Log.
|>Windows Server 2003 will ask you if you want to save the contents of the file before clearing it. Click Yes and then choose a location to save the contents of the log.
|>Click Save. This will back up the contents of that log and clear it.
Follow these steps to change the size of a log:
|>Right-click the log file object for which you wish to adjust the size and select Properties.
|>Enter the new file size in the Maximum Size box (the default is 512 KB), then click OK.
Maintaining log files automatically
When the log files are created, they are assigned a default size of 512 KB. This size is usually easy to manage; however, if the system is accessed frequently and processes many logons, the Security log may become full more often than you like. If this happens, the PC will prevent logons by anyone who is not a member of the administrators group. (This is typically not an issue on a server system, but I'm using it as an example of an event that can occur that will fill the log file.)
To remedy full log files, you can assign one of the following actions to each log file:
|>Overwrite events as needed (overwrite the oldest events first)
|>Overwrite events older than xx days
|>Do not overwrite events (clear logs manually)
If you assign either of the first two options, it will allow the logs to manage themselves in terms of disk space.
Note: it's important to review log files on a regular basis to ensure that your Windows Server 2003 systems are functioning properly. The log archiving option will allow you to review the log files, while keeping the active logs manageable with little intervention.
More...
http://www.builderau.com.au/program/windows/soa/Using-the-Windows-Server-2003-Computer-Management-Console-Event-Viewer-snap-in/0,339024644,339286671,00.htm
Thursday, September 25, 2008
Creating a Master Site Template in Dreamweaver
In this article, I'll provide you with a bunch of cheesy sample images for a pretend web page template. But I'll also provide you with concrete, albeit basic, information regarding how to create a master template for a web site using Dreamweaver 2004 MX.
Creating a template in Dreamweaver is very similar to creating a template in Microsoft Word or other programs. You need to design and/or add all the static elements that will become part of the template...items that you want to appear on every subsequent page that will be created from this template.
The template must also be saved as a template and saved into a Template directory within the project site files. Then, whenever you need to create a new page for your web site, you just create the new page from the master template designated to that site. Furthermore, you'll save lots of time modifying your site, because if you add information to the template, it will be added to all the pages of your site. This makes updating or adding links quite simple. It also helps to ensure consistency...a sure sign of a professional site. And it also helps avoid errors because you won't forget to update one page, since all pages are tied to the template update.
There are many ways to layout a template, but one of the most common ways is to use a Layout Table. You can think of it as adding a main table to the page, and then drawing out cells within that table. These cells become your content areas.
To start laying out your framework, you need to move into the Layout Mode. Click View > Table Mode > Layout Mode, as shown below.
More...
http://pubs.logicalexpressions.com/pub0009/LPMArticle.asp?ID=524
Dreamweaver templates
About creating Dreamweaver templates
You can create a template from an existing document (such as an HTML, Macromedia ColdFusion, or Microsoft Active Server Pages document) or you can create a template from a new document.
After you create a template, you can insert template regions, and set template preferences for code color and template region highlight color.
Note: Templates in Adobe Dreamweaver differ from templates in some other Adobe Creative Suite products in that page sections of Dreamweaver templates are fixed (or uneditable) by default.
For a tutorial on creating templates, see www.adobe.com/go/vid0157.
For a tutorial on using templates, see www.adobe.com/go/vid0158.
About editing and updating templates
When you make changes to and save a template, all the documents based on the template are updated. You can also manually update a template-based document or the entire site if necessary.
Note: To edit a template for a Contribute site, you must use Dreamweaver; you cannot edit templates in Contribute.
Use the Templates category of the Assets panel to manage existing templates, including renaming template files and deleting template files.
You can perform the following template management tasks with the Assets panel:
Create a template
Edit and update templates
Apply or remove a template from an existing document
Dreamweaver checks template syntax when you save a template but it’s a good idea to manually check the template syntax while you’re editing a template.
Build a .NET App for Google Checkout
01/09/2007
Google Checkout is a new service designed to make online shopping faster, safer, and more convenient by integrating with sites to help people pay for goods and services online. In this article, I'll explain how Google Checkout works, give you an overview of its API, and then show you how to develop an application for it using .NET. I've also included sample code for the application. (Full disclosure: I work for Google, where I help large merchants integrate with Google Checkout.)
To start, let's take Google Checkout for a spin. Buy.com is one of the merchants that have integrated with Checkout. If you go to Buy.com's website, put an item in your shopping basket, and click the Checkout link, you will see two ways of completing the purchase (Figure 1). You can either use Buy.com's regular checkout process, or you can use Google's Checkout.
More...
http://www.windowsdevcenter.com/pub/a/windows/2007/01/09/build-a-net-app-for-google-checkout.html?page=1
ASP.NET: How to Integrate Both Google Checkout and PayPal In 3 Steps
If you’re saying, “Wait a second, haven’t you already written an article on this?” you are correct. However, the solution I present to you here is infinitely simpler and requires fewer moving parts. The only reason I didn’t take the previous article down is because it does present interesting information about nesting MasterPages.
The Solution
In their documentation, PayPal and Google Checkout both mention that you must put their code into your site exactly as they have it, using the HTML forms they way they have structured them. This is not true. There are only a few bits of information that are required, and so long as they are present in an acceptable fashion, your pass-off to these gateways will work smoothly and flawlessly.
1. Get rid of your form tags.
2. Create image buttons for Google Checkout and PayPal
3. Create your hidden inputs to transfer information to PayPal and Google Checkout (from the same page, no extra postbacks!).
More...
http://dotnetdiscussion.net/2008/02/27/aspnet-how-to-integrate-both-google-checkout-and-paypal-in-3-steps/
JavaScript load placement
Programming for the Internet is fraught with a whole host of things that you can't depend on, but for the moment I'll be satisfied with talking about one of them: timing.
Any JavaScript that affects the way a page displays – either its content or its styling – has to first make sure that everything it requires is there i.e. that the page it's working on is downloaded (and parsed). Traditionally (well, for the past couple of years) this requirement has been met in one of two ways: placing an onload function call on the body element, or placing an automatically executed script late in the content of the page. However, these two methods have their disadvantages. Namely, that they can take a while to execute and thereby account for a page flicker where the content is visible before it has been transformed.
To demonstrate this, I've created an example page where a set of tables is hidden using JavaScript and a select box is used to display a particular one. There are four different pages of differing size (content after the tables) and each page has three different methods of running the JavaScript which hides the tables.
The third method is one of my own devising: a scheduling script that runs as soon as the "head" scripts are executed, but which checks to see if the required elements (the tables) exist yet. If they exist they are transformed, if they do not exist the script is scheduled to run after a short wait (1 millisecond), whereby it checks again ... Here's the results:*
Time taken to load JavaScript that hides page elements (Firefox)
body.onload
Content call
JavaScript scheduler
Small page 1103ms 1081ms 1062ms
Medium page 1128ms 1150ms 1134ms
Large page 1531ms 2621ms 1534ms
Image 11331ms 1849ms 1015ms
Time taken to load JavaScript that hides page elements (IE 6)
body.onload
Content call
JavaScript scheduler
Small page 2250ms 1644ms 1437ms
Medium page 2199ms 1522ms 1475ms
Large page 2256ms 1566ms 1509ms
Image 12556ms 3050ms 1628ms
*Times were averaged out over 5 attempts for each combination over a 56kb connection. Cache was cleared for each attempt. Timing of execution was initialised by the first script in the "head" and terminated when the function that hides the tables was executed.
At first glance, large differences can be seen in body.onload initialisation between Firefox and Internet Explorer. IE seems to only regard "body" as loaded until after CSS background images have been downloaded, whereas Firefox appears to treat "body" as loaded once its code has been downloaded and parsed.
The filesize of the web pages doesn't appear to affect JavaScript load times too greatly, but it can clearly be seen that the introduction of an image file adversely affects body.onload initialisation. Content calling and scheduling were on a rough par, but improvements could be seen in the scheduler for larger files and images.
Given the poor performance of body.onload under varying circumstances, it would appear that this is not a good option for the initialisation of page transforming JavaScript. Content calls could be an alternative, but they do not guarantee that the required content will be loaded, and they also require alteration of the page content itself. Scheduling of transformation appears to be the safer and faster option, although it still does not prevent flickering of content.
More...
http://www.themaninblue.com/writing/perspective/2004/09/29/
Javascript Q&A
A - JavaScript is parsed first (analyzed), and then it is executed (carried out). If an error is found in the code during the parsing phase, then the execution phase is canceled. If the JavaScript contains no errors, then the code is executed by the browser. In the context of a browser, this means that statements written in the global scope that are not functions, get executed.
Q - In what order is JavaScript executed in a browser?
A - Inline and external scripts are executed in the order in which they appear in an (x)HTML document. The contents of each script is parsed and executed before continuing on to the next script. It should be noted that the loading of an (x)HTML page is halted while loading external JavaScript files.
Q - In what order are (x)HTML pages and there assets loaded?
A - Browsers will loosely load an (x)HTML document in the following order:
(x)HTML is parsed by the browser
External scripts/style sheets are loaded
Scripts are executed as they are parsed in the document
(x)HTML DOM is fully constructed
img, embed, object, and iframe content is loaded
The page is finished loading and the JavaScript onload event is invoked
Q - What is the onload event?
A - The onload property of the window object specifies an event handler function that is invoked when a document or frameset is completely loaded into its window or frame. This property can also be set by using the onload attribute of the body element.
Q - Why isn't the window.onload adequate for all my DOM scripting needs?
A - There are two major limitations to the onload property. The first limitation is that this property can only accept one function. If you try to attach two functions to this event, the last one declared will be attached to the event and the first function assigned will be discarded.
The second limitation of window.onload is that the event fires only after everything in an (x)HTML document is loaded — including images, flash, and frames! Waiting for these elements to load before the onload event is fired can cause UI errors if the user tries to interact with the page before the JavaScript event handlers have been applied to the DOM via the onload event. Moreover, the user experience can really suffer if JavaScript functionality is delayed due to large assets being loaded into the browser.
Q - Why do I often see JavaScript written/included before the closing body element in an (x)HTML document?
A - DOM elements can not be accessed by JavaScript until the browser has loaded the HTML elements into the DOM. By placing JavaScript at the end of an (x)HTML document (before the closing body element), you will ensure that the script is called as soon as the DOM is constructed/loaded and ready for manipulation. An advantage of this approach is that JavaScript code is executed right after the DOM is constructed and possibly before the onload event would fire.
JavaScript beginners get tripped up by this constantly by placing code that manipulates the DOM in the header element of an (x)HTML document. This causes an error because the DOM has not yet been constructed and thus is not yet accessible to JavaScript that traverses/manipulates the DOM.
Q - Is JavaScript in the global scope still being executed even after the onload event is fired?
A - All JavaScript that is available when the browser first parses the page is executed before the onload event is fired. Of course, other events can trigger JavaScript execution after the onload event.
Q - Can you explain the difference between the following DOM event techniques: onload, DOM Ready, and Element Ready?
A - All of these techniques are essentially used to execute JavaScript only after the entire page has been loaded, the DOM has completely loaded, or the DOM has partially loaded in a web browser. Below I specifically discuss each technique.
onload - This technique is rather self explanatory. A Function assigned to the onload property of the window object will be executed once an (x)HTML document has been completely loaded by a web browser. For example:
view plaincopy to clipboardprint
//
window.onload = function(){ alert("page loaded") };
// //
window.onload = function(){ alert("page loaded") };
//
Since only one function can be assigned to this property at a time, many developers started using an event utility script to add multiple onload handlers to a web page. You might be familiar with the original addevent script, and its numerous predecessors.
DOM ready - This technique tries to improve upon the onload technique by executing javascript code once the DOM is constructed, and before the page has actually finished loading. How this is done has been the topic of numerous blog posts.
Element ready - This technique attempts to surpass the DOM ready technique by checking the DOM loading status at intervals for the availability of a specific element. Doing this will allow for the execution of JavaScript DOM manipulation code as soon as the element itself, but not necessarily the entire DOM, is ready.
Q - Can I assign an event handler to window.onload, and at the same time set the onload attribute of the body element to a different event handler?
A - No, providing a value to the onload attribute of the body element will override any event handlers you assign to the window object.
Q - What is meant when it is said that client-side javascript is single threaded?
A - This means that the parsing of (x)HTML documents stops while scripts are loaded and executed, and that web browsers stop responding to user input while event handlers are being executed.
This is a good thing, and a bad thing. It's good because you can rest comfortable knowing that two event handlers will never run at the same time. Also, you can manipulate document content knowing that no other thread is attempting to modify the same piece of content.
It's bad in that intensive scripts can hold up the user experience by causing periods of unresponsiveness from a JavaScript driven UI.
More...
http://javascriptant.com/articles/
http://javascriptant.com/articles/10/qa-on-javascript-execution-onload-techniques
Tuesday, September 23, 2008
Step-by-Step tEarn install on Google's Blogger
tEarn Exitmercial NetworktEarn (Tag, Earn) has unveiled our multi-media, full page, exitmercial network. Success of the tEarn community promises: (1) 50 to 100 times higher eCPMs for publishers and bloggers (2) lower CPC and multi-fold ROI improvements for buyers. 50 out-of-the-box innovations enable this new marketplace. We're ready for phase two beta open enrollment. Future phases may require writer qualifications. Learn more at ady.tearn.com.
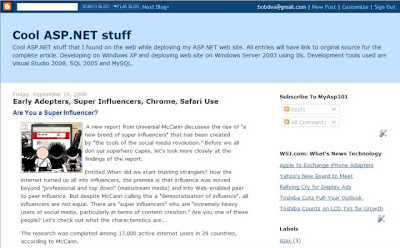
Create a tEarn Account
Saturday, September 20, 2008
Want to be the next Google? Create enduring values
Editor's note: This is an op-ed piece by Bernard Moon, vice president of holding company The Lunsford Group.]
Last week I was having lunch with a senior person involved with Facebook and asked him about the recent departure of some of their key people. His response: “Facebook just doesn’t have the right culture. They’re not a Google or Microsoft.”
This statement kicked off an interesting conversation. My lunch companion argued that a company’s culture and founding values are significant factors in a startup’s march towards long-term success. We also touched on the importance of leadership in a startup, and whether Facebook has the right team running it to become the next Google.
Later that week, my colleague, Dan Wooldridge, who provides leadership consulting to established enterprises when he’s not busy with the operations of our various entities, brought up the founding of Sony. Dan told the story of how in 1946, as Japan was rebuilding itself after World War II, Masaru Ibuka and Akio Morita started Sony with just a mission, before an actual product was made. Ibuka wrote:
The first and primary motive for setting up this company was to create a stable work environment where engineers who had a deep and profound appreciation for technology could realize their societal mission and work to their heart’s content.
They also stated that they wanted to:
• Establish an idea factory that stresses a spirit of freedom and open-mindedness, and where engineers with sincere motivation can exercise their technological skills to the highest level.• Reconstruct Japan and elevate the nation’s culture through dynamic technological and manufacturing activities.
It is amazing that Ibuka and Morita had the fortitude and long-term perspective to accomplish these founding goals. Although it took decades, Sony did eventually elevate Japan’s national reputation in the world as a leader in technology and consumer products. This was a reflection of Ibuka and Morita’s strength in leadership, of their values, and of how they created a corporate culture where stated values led to tangible behavior and results.
These two discussions made me think about various companies I’ve encountered over the years, and how their core values, leadership, and related factors drove them to become the titans of their industry.
Cultivate your core values. What enduring core values do you want your startup to live by? How do you plan to execute on them? One of Google’s core values was having the smartest, most competent people working there. Google executed on this by requiring job applicants to submit their college transcripts and standardized test scores (i.e., SAT, GRE, GMAT), and having minimum standards for GPAs. Google even requires this for senior hires, when most companies stop asking for transcripts above the middle manager level.
I always thought this was impractical—since some talented and successful executives do not have the best GPAs—but Google sticks with this measurement as a method to execute on its core value. I admire that, even though I don’t completely agree with Google’s implementation. (Yes, Google makes some exceptions to this guideline, but generally stands by these requirements.)
Another value is being “Googley.” When Googlers interview a candidate, they have to ask themselves, “Is this person Googley? Are they nice? Is this someone I want to work with?” It’s rare for companies to ask such questions, but this is something the founders wanted to be a part of Google’s culture. Of course the company has experienced tremendous growth over the years—from approximately 3,000 in 2004 to over 19,000 in 2008—so it is more difficult to execute on this value (I’ve met a fair amount of Googlers who aren’t so Googley), but it’s still commendable to stick to this philosophy.
Being Googley might not have helped Oracle grow into one of the largest software companies, since its market probably needed the hyper-aggressive sales culture that the company is known for. Oracle valued the characteristics that make up its sales-oriented culture, so it hired people who were very competitive and hard-charging throughout the company.
Apple’s Steve Jobs created a company that values creativity and an intense pursuit of perfection. Apple has become a unique force in the consumer electronics market by rejecting the common value of listening to its customers and believing that Apple knows what people really want. So you have to create core values that reflect not just the founding team’s values, but also what is needed to succeed in your target market.Venture capitalists make a difference. While some entrepreneurs don’t want to hear this (and a disclaimer — I’m not a VC), VCs can make a difference. When my wife joined Google in 2004, some of their operational processes, such as performance reviews, were presented to her as “John Doerr, one of Google’s investors, helped establish this process based on his previous experience….” I thought it was interesting that his lore and impact were still proffered five years after Google’s founding, and how this shows the effect a great VC can have on your company. Sequoia’s legendary Don Valentine is known for his tremendous influence on the founding of Atari, Apple, Cisco, and Oracle. There are also relative newbies like Bessemer Venture Partners’ Dave Cowen, whose 45 early-stage investments have produced 19 public companies and 18 acquisitions. So getting smart money is important.
Not everyone will be funded by Kleiner Perkins, Sequoia, Benchmark, DFJ, or other top firms, but as an entrepreneur you really need to do due diligence on potential investors. What is their track record? How hands-on are they? Is that the right level for you? Do prior entrepreneurs endorse them? Would they work with these VCs again on their next startup? Do you trust this person?
Don’t compromise on hiring. Truly making your core values tangible within your startup really begins with the founding team and early employees. Assuming that you and any other founders are effective leaders, the rest of your path to execution will be far easier when you work with outstanding people who completely believe in your core values and vision. In the “Letter from the Founders” written by Larry Page and Sergei Brin for Google’s IPO filing, they emphasize the core of Google’s values:
Our employees, who have named themselves Googlers, are everything. Google is organized around the ability to attract and leverage the talent of exceptional technologists and business people.
During the early days of Microsoft, when Bill Gates was asked who his greatest competitor was, he answered “Goldman Sachs.” He didn’t see Apple or IBM as his top competition—rather, it was Goldman Sachs which was competing with Microsoft for the top talent from colleges and graduate schools.
In many people’s minds, Google has recently taken over Microsoft’s mantle of technology’s top player, while maintaining its ability to attract top talent. For example, for as long as I can remember—until the last two years—the top destinations for MBA graduates have been either Goldman Sachs or McKinsey. But for the past two years, Google has been named the most desired company to work for by MBA students. Talent attracts talented people.
Naturally it’s easier to attract the best talent when you’re Google, Microsoft, or a hot company like Facebook. But they too started out as small companies, and no one knew if it would be good to work there. For early-stage companies, I cannot emphasize it enough: Don’t compromise on the skills, personality, and values you want in your hires. Do your reference checks thoroughly, ask probing questions, and don’t rush to judgment because you’re paddling upstream with a spoon in Startup River and your colleagues are begging for more help. In the early stages of your company’s growth, every hire—from top engineer to admin—really makes a difference.
Leadership holds it together. Founders need not just the talent, discipline, and fierce determination to succeed, but also the flexibility to create new paths for the company. Many successful companies have changed their business models mid-stream, so the founders must be determined and focused, yet open to the realities of the market. Those realities can include the fact that the product or service might be too early, that they need to be further developed, or, unfortunately, that the company needs to be shut down.
Sometimes the founding CEO isn’t the right person to take a company to the next level—and has to have the humility to recognize this. Google’s Page and Brin realized that they needed an Eric Schmidt to help grow their company, and I believe Google would not have been as successful without adding Schmidt to the mix. EBay’s Pierre Omidyar eventually needed Meg Whitman to take the CEO role for its next stage of growth. There are exceptions, such as Bill Gates, Larry Ellison, Jeff Bezos, and Steve Jobs—founders who continued or returned to lead their companies long past startup and IPO stages.
Yet most entrepreneurs won’t know whether they are able or want to lead their company through all of its growth until they’re there. Sometimes an unfortunate collision occurs with bitter emotions, an entrepreneur getting thrown out justly or unjustly, and a board hoping the next CEO will be the right leader. Other times an entrepreneur recognizes that he or she isn’t the right person for the next stage, and helps find the right person to maintain the company’s values while executing on a grander scale. And whether under old leaders or new, that is the most important outcome—having the core values endure through all stages of a company’s growth.
So, as you’re writing your business plan and slides, remember to have meetings about what you want your company’s core values to be and how you will execute on them. If you never had this critical discussion yet, take some time to do so. Who knows? If you’re bold, maybe the incredible will happen, and your company will become the next Google.Bernard Moon is vice president of the Lunsford Group, a private holding company consisting of entities in technology, media, research & consulting, health care, investment boutique, and real estate.
Bernard blogs at Silicon Moon.
http://venturebeat.com/2008/09/17/want-to-be-the-next-google-create-enduring-values/
You can serve video ads using Youtube
- Upload your video at Youtube. The video can be any length. The time limit depends on your message and the patience of your intended reader. Industry wisdom suggests 15 seconds. Microsoft has tested 90 seconds. It can even be a 30 minute program, but few people can be interrupted for a 30 minute show.
- For each video, Youtube provides an 'embed' tag. Click and copy the tag to the clipboard.
<object height="344" width="425"> <param name="movie" value="http://www.youtube.com/v/fkZnJsz1FRk&hl=en&fs=1"></param> <param name="allowFullScreen" value="true"></param> <embed src="http://www.youtube.com/v/fkZnJsz1FRk&hl=en&fs=1" type="application/x-shockwave-flash" allowfullscreen="true" width="425" height="344"></embed> </object>
- Sign into your account at http://ady.tEarn.com/
- Click Advertiser on the left menu. This is your ad cart.
- Edit an existing template or create a new template.
- Paste the embed tag into the supplied textbox.
<object height="500" width="770"> <param name="movie" value="http://www.youtube.com/v/fkZnJsz1FRk&hl=en&fs=1"></param> <param name="allowFullScreen" value="true"></param> <embed src=" ... " width="770" height="500"></embed> </object>
Continuous Loop<embed src="http://www.youtube.com/v/fkZnJsz1FRk&hl=en&autoplay=1&fs=1"></embed>
To repeat and restart the video, insert &loop=1 as follows:
<embed src="http://www.youtube.com/v/fkZnJsz1FRk&hl=en&loop=1&fs=1"></embed>
Friday, September 19, 2008
Early Adopters, Super Influencers, Chrome, Safari Use
Are You a Super Influencer?
A new report from Universal McCann discusses the rise of "a new breed of super influencers" that has been created by "the tools of the social media revolution." Before we all don our superhero capes, let's look more closely at the findings of the report.
Entitled When did we start trusting strangers? How the internet turned us all into influencers, the premise is that influence was moved beyond "professional and top down" (mainstream media) and into Web-enabled peer to peer influence. But despite McCann calling this a "democratisation of influence", all influencers are not equal. There are "super influencers" who are "extremely heavy users of social media, particularly in terms of content creation." Are you one of these people? Let's check out what the characteristics are...
The research was completed among 17,000 active internet users in 29 countries, according to McCann.
Who Are The Super Influencers?
Super influencers are heavy social media users, who also "fit the typical profile of early adopters who are likely to try new products, take risks and share their opinions with friends."...
Chrome Market Share: WebTrends Says 2%; Over 7% at ReadWriteWeb
Web analytics firm WebTrends reported today that mainstream Internet users are "embracing" the Google Chrome browser. In the third week since its launch, WebTrends states that Google Chrome is the fourth most popular browser used by visitors to the web site of The Daily Telegraph, Britain's highest selling newspaper. WebTrends puts the figure at "nearly 2 percent" of the total traffic to telegraph.co.uk, which it says is more than Netscape, Mozilla, Opera and other browsers. Presumably the browsers above it are IE, Firefox and Safari.
Here at tech-focused site ReadWriteWeb, the last couple of weeks of Google Analytics data shows that about 7.25% of our readers are visiting using Chrome.
Here's a screenshot of RWW stats from the last couple of weeks:
Compare this to the month of August, when our browser stats looked like this:
Clearly Chrome has taken share from both Firefox (3.93%) and IE (4.7%), for our tech-savvy readers. However Safari's share has gone up a little on our site in September. Time will tell whether these trends continue, but for now Chrome is continuing at a solid 7% + for our site. Not bad when you consider that our readers are also statistically more likely than the general population to use Macs - which Chrome isn't available on yet. 18.28% of our August readers were Mac users, with 75.68% Windows.
More importantly, Chrome looks to be close to establishing itself as the 4th most popular browser in the mainstream market - which is bad news for Opera.
Step-by-step guide to add tEarn to your Blog
Step-by-Step tEarn Install on Google's Blogger
If you don't already have a blog then
go to http://www.blogger.com to create your new blog.
Follow the 3 easy steps to create a blog
Create a tEarn Account
Go to http://ady.tearn.com
Select "Sign In" upper right corner
If you already have an account sign in and select "Log In" button.
Skip to the "Setup your Publisher Profile page" slide
If you do not already have an account press the "Sign Up" link.
Select a user name and fill in the blanks.
After you have filled in the information select the "Done" button
Press the "Continue" button
Optionally fill your profile information and
the press "Update Profile" button
Setting up your Publisher Profile
Select the "Publisher" link on the left most navigation tree
The Publishers control is displayed
Select the "Show" button to open up the "Add Website" dialog
Enter thew domain of your web site
Select "Show" under "Join a Channel" to open up the Channel selection dialog.
in the example we selected "Life"
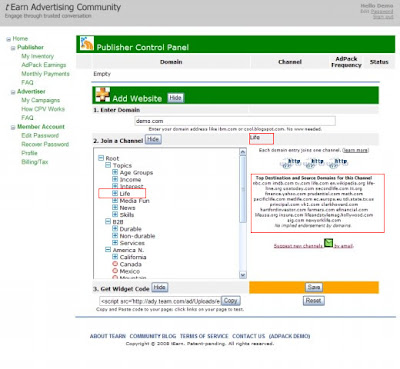 Select the "Get Widget Code" "Show" button to display the tEarn code snippet that you will include on your blog.
Select the "Get Widget Code" "Show" button to display the tEarn code snippet that you will include on your blog.Select the "Copy" button to copy the code snippet to the clipboard.
 Pasting the code snippet in to your blog
Pasting the code snippet in to your blog
Login to Blogger
Select "Layout" tab
Select the "Edit HTML" tab
Scroll down to the bottom just before "/body "the tag and paste the tEarn code snippet
Select "SAVE TEMPLATE"
Your blog is ready to display tEarn Ads!!
All external links will display Ads
Thursday, September 18, 2008
Using the AJAX Timer Control as an UpdatePanel Trigger
A .Net Developer's Blog
In the web application I am currently developing there is a page which allows user's to start an off-line process. There are a number of parameters the user can configure that will effect how long each of the processes take to complete. When the system in under a typical load an operation can take anywhere from 30 seconds to 30 minutes depending upon how it is configured. After the user kicks off the operation, we redirect them to a status page that contains a list of all of the finished, queued and currently executing operations in the system. The idea being that the user could see where there process is in the queue so they could get an idea of when it might complete.
After the page was in production for a few months, we started getting feedback from our users saying they would like it if this status page would automatically refresh every 30 seconds or so so they can continuously view the most up to date state of the jobs running within the system.
I figured it would be pretty simple to meet the user's requirements by adding an ASP.NET AJAX Timer control to the page. The Timer Control will automatically postback the page at a specified interval. If I use the Timer as an AsyncPostBack trigger for an UpdatePanel (which I believe it the primary use case for the Timer control), it should provide exactly the functionality I need. Here are the steps I followed and few items that I learned along the way ...
Overview of the ASP.NET AJAX Timer
The ASP.NET AJAX Timer Control will perform postbacks at a predefined interval. The Timer has an Interval property that determines how often the Timer fires. When the Timer Elapsed period passes the Timer's Tick event fires on the server.
If you want the complete page to postback (a full postback), you can just place the Timer on the page just like normal. If you want the Timer to trigger an partial postback, you have 2 options:
Place the Timer inside an UpdatePanel
Place the Timer outside of an UpdatePanel and explicitly register it as an AsyncPostBackTrigger
Additionally, the Timer properties (primarily Enabled and Elapsed) can be modified within the Timer's Tick event handler. Allowing you to modify these values at runtime if you detect that you need to.
As far as adding the Timer to the page, that's pretty much it. However, there are a few considerations you should think about when using the Timer.
AJAX Timer Considerations
The behavior of the Timer differs slightly depending upon if it is contained inside or outside of an UpdatePanel
Depending upon where the Timer is on the page dictates how the Elapsed value is calculated.
If the Timer is outside of an UpdatePanel it continues to run during a partial postback. So if the Elapsed property is set to 5 seconds, and the partial postback takes 3 seconds, the timer will fire again 2 seconds after the partial postback completes.
When the Timer is contained within an UpdatePanel, it stops running while the postback is executing and starts again when it finishes.
Set the Elapsed property to a value that is large enough to allow the Tick server event handler to finish executing. Because the Timer's placed outside of an UpdatePanel continue to run during the partial postback, if the partial postback doesn't complete before Elapsed passes again, the currently executing request is canceled and a new one is initiated. This is probably not what you want to happen.
Turn off the Timer when it isn't needed anymore
The Timer will continue to run until the user navigates away from the page or until you programmatically set the Enabled property of the Timer to 'false'. If you have a way to determine that the Timer is not needed anymore, go ahead and save the network some bandwidth and turn off the Timer.
More...
http://mattberseth.com/blog/2007/08/using_the_ajax_timer_control_a.html
Tuesday, September 16, 2008
CPC (cost per click) model is flawed
On the publisher side things are even worse. Google doesn’t share enough revenue with content sites that show their ads. The only thing keeping them even close to honest is the fact that Yahoo and Microsoft will occasionally compete for those partners. Take that away, and Google will go back to keeping the majority of advertising revenue generated at those sites (their only competition will be other types of advertising, which generate far less revenue). That is a terrible outcome when you look at it from the perspective of the health of the Internet. ..."
from TechCrunch by Michael Arrington
We agree.
http://ady.tearn.com
Wednesday, September 10, 2008
Opening New Browser Windows
A HREF="link.html" TARGET="_blank"
Note that the proper target is _blank, in all lower case. There are many mistaken impressions among Web authors of what the correct target is, aided and abetted by the fact that the popular browsers do in fact open up a new window when given any unrecognized target name, but the proper target according to the formal HTML specs is _blank (with an underscore as its first character).
More...
http://webtips.dan.info/new-window.html
Tuesday, September 9, 2008
Creating time delays in Javascript
There are two ways of creating time delays with JavaScript. The first is more simple and will simply wait for a specified amount of time before executing a function. The second does the same but will repeatedly execute the function.
Note, most browsers have a minimum delay length of between 25 and 75 ms. If a shorter delay is specified, the actual delay will be the minimum delay length. Even with higher numbers, the delay is never perfect. Most browsers will take slightly longer than the time you ask for, typically just a few miliseconds error. Some may correct their errors over time with interval timers. Also note, setting many timers with short delays on one page will cause the browser to become slow and somewhat unresponsive. Three or four timers is usually the reliable limit.
setTimeout
The first method uses a window method called setTimeout(). The method waits for a specified number of milliseconds then executes the specified code. The code can either be a direct reference to a function, or it can be a string that will be evaluated as if it contained source code.
window.setTimeout(referenceToFunction,timeInMilliseconds);window.setTimeout('runMoreCode()',timeInMilliseconds);Wherever possible, you should use a direct function reference as it is much more efficient. Using a string requires the browser to create a new script environment so it can process the script.
If you create a timeout, the code after the call to setTimeout will continue to run as normal. After the specified delay, the timeout will start a new thread, and the code specified in the call to setTimeout will be run in the new thread, along side any code that is still running in the initial thread. Unlike with many more complex languages, JavaScript does not offer any way to control when those threads sleep, wake, or yield. The JavaScript engine handles all of that, and you must accept that your new thread could be executing at any time next to another thread. Many JavaScript engines will simply allow one thread to complete before allowing the other thread to start. The same applies to events, which run in their own threads, and can be triggered at any time.
More...
http://www.howtocreate.co.uk/tutorials/javascript/timers
RSS Reader using ASP.NET 2.0 and C# 2005
RSS Feed is very popular in Internet. This tutorial will show you how to create a RSS Reader using ASP.NET 2.0 and C#.
In this sample, we created a simple function to process the RSS feed from a sample URL. This function define a string of rssURL as its parameter. This string contains the RSS's URL. It will use the value of rssURL to create a WebRequest.
WebRequest is the abstract base class for the .NET Framework's request/response model for accessing data from the Internet. An application that uses the request/response model can request data from the Internet in a protocol-agnostic manner, in which the application works with instances of the WebRequest class while protocol-specific descendant classes carry out the details of the request.
Requests are sent from an application to a particular URI, such as a Web page on a server. The URI determines the proper descendant class to create from a list of WebRequest descendants registered for the application. WebRequest descendants are typically registered to handle a specific protocol, such as HTTP or FTP, but can be registered to handle a request to a specific server or path on a server.
The response to this request will be put into WebResponse object. The WebResponse class is the abstract base class from which protocol-specific response classes are derived. Applications can participate in request and response transactions in a protocol-agnostic manner using instances of the WebResponse class while protocol-specific classes derived from WebResponse carry out the details of the request. Client applications do not create WebResponse objects directly; they are created by calling the GetResponse method on a WebRequest instance.
After then, the WebResponse object will be used to create a stream to get the XML data. Stream is the abstract base class of all streams. A stream is an abstraction of a sequence of bytes, such as a file, an input/output device, an inter-process communication pipe, or a TCP/IP socket. The Stream class and its derived classes provide a generic view of these different types of input and output, isolating the programmer from the specific details of the operating system and the underlying devices. The we used a XmlDocument to store the stream data. XmlDocument manipulating the data of XML, finally read the RSS contents from Feed.
More...
http://www.aspnettutorials.com/tutorials/xml/rss-aspnet2-csharp.aspx
ASP.NET AJAX RSS Reader
An ASP.NET AJAX RSS reader.
Introduction
So the other day, I was adding a “news page” to one of my projects, and thought it was a great chance to play with consuming some other RSS feeds that had related information to what I was working on. So, I started looking round, and found the RSS Toolkit that had an RSS Data Source control that is perfect for consuming RSS feeds – the toolkit actually does much more, you should have a read on Dmitry’s blog (he wrote the toolkit and is on the ASP.NET team) and download the toolkit here.
I have also used the ASP.NET AJAX Toolkit (which if you are unaware is a collection of controls for use with ASP.NET AJAX, it's an open source project with contributors from both MS and the community). The control I use is the Collapsible Panel control, so you can see a list of the blogs and click each to reveal the text.
Background
You will need to have the ASP.NET AJAX RC1 extensions installed, which you can get from here.
Using the code
Simple page layout using CSS, the right panel contains a DataList control bound to the RssDataSource to display the blog items, the DataList control is wrapped in an asp:UpdatePanel. The item template in the DataList has a collapsiblepanelextender from the AjaxControlToolkit to display the description of the blog item.
Changing the selection of blog to view files, the asp:UpdateProgress panel is set to display, and the blog items are loaded and displayed. You can see on the blog list that I have simply shaded the background of the
More...
http://www.codeproject.com/KB/ajax/AspNetAJAXRssReader.aspx
Consuming Membership and Profile Services via ASP.NET AJAX
ASP.NET 2.0 introduced various application services—such as Membership, Roles, and Profiles—that eliminate a lot of coding that was required to provide the same functionality. However, these services are part of ASP.NET's server-side framework, which could pose a challenge when you use ASP.NET AJAX to consume the services from client-side JavaScript code. Fortunately, ASP.NET AJAX provides an out-of-the-box solution to this problem. This article explains how to use this solution in C# with Visual Studio.
Sample Scenario
Suppose you are developing a new web site and want to implement forms authentication. The web site will have a user registration page, a login page, and one or more pages that you must secure. The user registration and login pages use ASP.NET AJAX for an enhanced user experience. Also, the site must capture details such as birth date and address at the time of registration. This information is to be stored in the Profile of the user.
To develop a web site that fulfills all the above requirements, begin by creating a new ASP.NET AJAX-enabled web site with C# (see Figure 1).
More...
http://www.developer.com/net/asp/article.php/10917_3661801_1
Monday, September 8, 2008
A Custom ASP.NET Server Control for Displaying RSS Feeds
When creating this recommended blogs page, I decided rather than merely listing links to the various blogs, I'd like to also show the title of each recommended blog's most recent entries. This task is not too difficult to accomplish because blogs typically provide an RSS syndication feed. RSS is a standard that spells out a format for syndicated content in an XML format. (For the specifics of the format, see the RSS 2.0 specification.) There are a number of programs, called aggregators that are designed specifically to organize syndicated content. Some free aggregators build using the .NET Framework include SharpReader and RssBandit. You can also easily build your own aggregator, as I described in this article: Creating an Online RSS News Aggregator with ASP.NET.
Initially I decided to just use the techniques described in an earlier 4Guys article, Consuming an RSS Feed with ASP.NET, which demonstrates how to display the items in an RSS feed in a data Web control. However, the code to implement this technique, while only a few lines of code long, seemed overly complex for the simple task I was after. Furthermore, the code, as-is, does not employ any caching of the RSS data, which not only leads to longer load times on my end (since the content must be grabbed from a remote Web server on each page load), but is also bad netiquette since it greatly increases the bandwidth sucked down from the server hosting the blog. What I wanted to be able to do was the following: add a Web control to my ASP.NET Web page and with one or two lines of code, at most, have the control display the items from an RSS feed. Too, the control should cache the downloaded RSS feed for a developer-specified number of minutes.
To solve this problem I decided to create a custom ASP.NET server control, which I call RssFeed. RssFeed is an open-source control, with complete source code available for download and modification at the RssFeed GotDotNet Workspace. This article explains how to obtain, install, and use RssFeed in an ASP.NET Web page. For technical information about RssFeed and its source code, be sure to consult the RssFeed Project Page.
Downloading RssFeed
You can download the code and/or a compiled assembly for the RssFeed server control by visiting the Releases Archives for the RssFeed GotDotNet Workspace. From the archives, you can download the entire source code or a pre-compiled assembly (.dll file). (Note: the compiled assembly was compiled using Visual Studio .NET 2003, and is therefore targeted for the .NET Framework Version 1.1. If you need to use RssFeed for .NET Framework 1.0, you will need to download the source code and compile it through Visual Studio .NET 2002.)
If you download the source code, before using RssFeed in an ASP.NET Web application you'll need to compile the source code. If you have Visual Studio .NET, this task is simple - simply double-click the skmRss.csproj file in the downloaded code files, which will open Visual Studio .NET. Next, go to the Build menu and choose Build Solution. That's it! This will create the compiled assembly - skmRss.dll. (If you are going to be using RssFeed in an ASP.NET Web application on a Web server running the .NET Framework Version 1.1, you can just download the pre-compiled assembly instead, if you want to skip the step of compilation yourself...)
Using RssFeed in an ASP.NET Web Application
The first step to using RssFeed in an ASP.NET Web application is to add the assembly, skmRss.dll, to the Web application. If you are building your ASP.NET Web application using Visual Studio .NET you can accomplish this by adding the assembly to the References folder. From the Solution Explorer, right-click on the References folder, Browse to the skmRss.dll file, and click OK. If you are not using Visual Studio .NET, simply copy the skmRss.dll file to the Web application's /bin directory.
If you are using Visual Studio .NET you can, at this point, add RssFeed to the Toolbox. To accomplish this, right-click on the Toolbox in Visual Studio .NET and select Add/Remove Toolbox Items (the exact wording differs between Visual Studio .NET 2002 and 2003...). Browse to the skmRss.dll file and click OK. This will add a control called RssFeed to the Toolbox. To add the RssFeed control to an ASP.NET Web page simply drag the control from the Toolbox onto an ASP.NET Web Form's Design tab. As you can see in the screenshot below, RssFeed provides a rich design-time experience with Visual Studio .NET.
More...
http://aspnet.4guysfromrolla.com/articles/102903-1.aspx
W3 Scools, HTML, CSS Javascript, XML, Etc..
The Largest Web Developer Site on the Net.
At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP.
More...
http://www.w3schools.com/
Securing Your .NET Web Services
Security has often been the neglected stepchild of software development, but it is increasingly coming under closer scrutiny. As Web Services are deployed in greater numbers, the security of these access points into an organizations business processes can no longer be relegated to backseat status.
Generally, you will have three general security scenarios for a Web Service:
Those that are open to the general population, with no authentication
Those that are open to the general population, but with authentication
Those that are open to a controlled sub-set of users, such as a companys employees
For this article, we'll assume that some sort of security is required. In addition, to simulate the scenario that will be common for many Web Services, we'll assume that the user base of our Web Services will not be confined to those users within our intranet.
At this point it is important to define several terms that are used in the context of IIS and ASP.NET security:
Authentication is the process of determining the identity of the requester, and whether that identity exists within the set of known users.
Authorization is the process of determining if a given identity has the rights to perform a requested action.
Impersonation is the process of accessing resources as another user. In this case, it would be an ASP.NET application or Web Service accessing resources using a users permissions, rather than the default user account under which ASP.NET runs.
Because .NET Web Services are based upon IIS and ASP.NET, the security model for Web Services is inherited from these technologies. However, Web Services will have different considerations than ASP.NET applications when developing a security strategy. Obviously, Web Services do not have user interfaces with which users can interact.
You can think of the available security services as layers (see Figure 1 below). These layers sit upon one another, can be used in various combinations, and are provided by either IIS or the ASP.NET runtime. These various security implementations will be discussed in the next section.
More...
http://dotnetjunkies.com/Tutorial/5D8B6D51-97B7-4825-B919-49A721A3FDF6.dcik
Regular Expression Library
More...
http://regexlib.com/DisplayPatterns.aspx
Server-Side Validations Using Regular Expressions
Introduction
SQL Server Application Platform Optimization
Download this whitepaper for a ready-made solution that delivers comprehensive infrastructure optimization in accordance with Microsoft’s APO model using HP PolyServe software in conjunction with HP BladeSystem c-Class products and Microsoft SQL Server Enterprise Edition.»
Simplified SQL Server Deployment and Management
Download this whitepaper for an efficient approach to SQL Server deployment and management with HP PolyServe Software for Microsoft SQL Server. The software supports both Microsoft SQL Server 2000 and SQL Server 2005, and includes a component called Matrix Server, which is shared data clustering software. It allows groups of servers and storage to work and be managed together flexibly to satisfy application requirements. »
Consolidating Microsoft SQL Server
The phenomenal success of Microsoft's SQL Server database has led to "SQL Server sprawl," which can be costly due to inefficient use of hardware, software, and administrative resources. Learn how HP's PolyServer Software for Microsoft SQL Server can consolidate SQL Server environments and improve resource availability. »
Easing the Migration to Microsoft SQL Server
SQL Server 2005 is quickly becoming the database solution of choice. The task of SQL Server 2005 migration need not be as difficult, time-consuming, or costly as one might anticipate. Software tools like HP PolyServe Migration Manager can dramatically reduce the complexity of migration and slash deployment time by up to 66 percent. »
Validating user input is the bane of every software developer's existence. Having one module that addresses all the user inputs greatly reduces the number of validating errors. Writing a single routine that does all the validation would be very difficult and tedious. The Regular expressions tool, however, can be used to validate all user inputs. It can make your code faster, more efficient, and less error prone. Regular expressions are a powerful tool for searching and processing text, and even in its simplest form, can make many complex tasks easy. This article provides a brief tutorial on the basics of Regular expressions and shows how the module can be extended to test border conditions.
Regular Expressions: What are They?
Regular expressions are a tiny, highly specialized programming language. They used to only be familiar to Unix users. Text editors like vi allowed regular expressions-formatted searches. Finally, Microsoft decided to give the same power to us and implemented it in Interdev. Most likely people haven't noticed it when they are using Find in Interdev.
When Microsoft started creating scripting languages for the Windows platform, only JScript contained regular expressions, leaving VBScript alone in the dark. That changed with version 5 of the VBScript engine. To ensure that Visual Basic (VB) developers can use regular expressions, the VBScript regular expressions engine has been implemented as a COM object. This makes them much more powerful, since they can be called from various sources outside of VBScript, such as Visual Basic or C.
Regular expressions provide tools for developing complex pattern-matching and textual search-and-replace algorithms. Any Perl, egrep, awk, or sed developer will tell you that regular expressions are one of the most powerful utilities available for manipulating text and data. By creating patterns to match specific strings, a developer has total control over searching, extracting, or replacing data. In short, to master regular expressions is to master your data.
A regular expression is a series of characters that define a pattern. The pattern is then compared to a target string to see whether there are any matches to the pattern in the target string.
Patterns
Regular expressions are almost another language by itself. A pattern defines the criteria to search for within a string. Regular expressions can be as simple as plain text, or use a unique language consisting of special characters and modifiers to build these patterns.
Alphabetic Data:
In a regular expression, the period (.) represents exactly one occurrence of any character other than a new line. Thus, the regular expression m.n will be matched not only by man, but also by remind and mint, since each of them contain an m and a n separated by exactly one letter.
Numeric Data:
So far we have seen the string patterns. Let's see how to match numeric data. If you want to match the numbers, \d should be used. \d matches one numeric character
More...
http://www.15seconds.com/issue/010301.htm
The Unoffical Cookie FAQ
1. INTRODUCTION
1.1 What is a cookie?
1.2 Where did the term cookies come from?
1.3 Why do sites use cookies?
1.4 Where can I get more information?
2. GENERAL QUESTIONS/MISCELLANEOUS
2.1 Introduction
2.2 Can I delete cookies?
2.3 How do I set my browser to reject cookies?
2.4 Are cookies dangerous to my computer?
2.5 Will cookies fill up my hard drive?
2.6 Are cookies a threat to my privacy?
2.7 Sites are telling me I need to turn on cookies, but they are on. What's wrong?
2.8 I deleted my cookies, and I can't log-on to my favorite site anymore. What can I do?
2.9 How did I get a cookie from doubleclick? I've never been there!
2.10 I looked at my Internet Explorer cookies, and they had my username on them! Can servers see my username?
2.11 There are two extra files in my Cookies folder called Mm256.dat and Mm2048.dat. What are they?
3. COOKIE FUNDAMENTALS
3.1 Introduction
3.2 How does a cookie really work?
3.3 Breakdown of Cookie Parameters
3.4 How do cookies end up on my hard drive?
3.5 What are all those entries in my cookies.txt file?
3.6 Where does MSIE keep its cookies?
3.7 Are cookies Year 2000 Compliant?
4. ADVANCED TOPICS
4.1 Introduction
4.2 Creating a cookie value
4.3 Retrieving a cookie value
4.4 Clearing a cookie value
4.5 Detecting if cookies are accepted
4.6 Compact Privacy Policies and IE6
More...
http://www.cookiecentral.com/faq/
System.Net.Mail FAQ
By Dave Wanta
This FAQ addresses the System.Net.Mail (SNM) namespace found in the 2.0 .NET Framework.
It starts with an Introduction and Programming Samples.
If you need to support the 1.x .NET Framework, be sure to check out my System.Web.Mail website here.
1 Introduction
1.1 What is System.Net.Mail?
1.2 What is the .NET Framework ?
1.3 What do I need to send email in .NET?
1.4 What is a relay server?
1.5 What is the IIS SMTP Service?
1.6 Can System.Net.Mail read email?
2 Exploring System.Net.Mail Classes
2.1 MailMessage Class
2.2 MailAddress Class
2.3 Attachment Class
2.4 SmtpClient Class
2.5 AlternateView Class
2.6 Linked Resource
3 Quickstart Programming Samples
3.1 Working with the Body
3.1.1 How do I send a plain text email?
3.1.2 How do I send a simple Html email?
3.1.3 How do I create a Multi-Part mime message?
3.2 Working with Addresses
3.2.1 How do I change the FROM address to a friendly name?
3.2.2 How do I change the TO address to a friendly name?
3.2.3 How do I specify multiple recipients?
3.2.4 How do I create a friendly non-ascii display name?
3.3 Working with Headers
3.3.1 How do I change the email priority?
3.3.2 How do I add the Reply-To header to the MailMessage?
3.3.3 How do I request a read receipt?
3.3.4 How do I add custom headers to the MailMessage?
3.4 Working with Attachments
3.4.1 How do I send an email with attachments?
3.4.2 How do I create an attachment from a stream?
3.5 Accessing Config File Mail Settings Programmatically
4 Advanced Programming Samples
4.1 How do I read SMTP configuration data?
4.10 How do I create a log file of the SMTP session?
4.11 How do I encrypt messages using s/mime or pgp?
4.2 How do I authenticate to send an email?
4.3 How do I change the SMTP port number?
4.4 How do I embed images in an email?
4.5 How do I send an email over SSL?
4.6 How do I send email asynchronously?
4.7 How do I write to the Pickup directory?
4.8 How do I send a web page?
4.9 How do I send non US-ASCII emails?
5 Troubleshooting System.Net.Mail
5.1 Bccs are not so blind.
5.2 Cannot enable SSL with a username and password.
6 Additional Help
More...
http://www.systemnetmail.com/